
DCShadow is an advanced feature of the Mimikatz tool, specifically found in the lsadump module. This powerful attack simulates the behavior of a Domain Controller (DC) by leveraging protocols like RPC, which are typically used by real DCs. The goal? To inject unauthorized changes into Active Directory (AD) without triggering common security controls, including those monitored by your SIEM.
How Does DCShadow Work?
DCShadow allows attackers to push changes to existing AD objects without leaving a trace in logs. Here are some examples of what an attacker could do:
- • Change a user’s primary group to the Enterprise Admin group (group 519).
- • Add the Enterprise Admin group SID to the
SIDHistoryattribute of an account. - • Re-enable a disabled account.
The Three Stages of a DCShadow Attack
- Registering a Fake Domain Controller
The attacker registers their fake DC by creating two objects in theCN=Configurationpartition and alters the Service Principal Name (SPN) of the compromised computer to pose as a DC. This step is critical for the attack’s success. - Injecting Data
Once registered, the attacker pushes malicious data to the AD. This is triggered through internal AD processes such asDrsReplicaAdd,KCC, or other AD replication events. - Cleaning Up
After completing the attack, the attacker removes the objects they created, effectively “demoting” the fake DC and covering their tracks.
Detecting DCShadow: Key Security Events
While DCShadow bypasses traditional logging, it still leaves traces through specific Windows security events:
- • Event 4742 (SPN Change): The first step of DCShadow involves altering the SPN of a computer. This generates event ID 4742 in Windows, where careful examination of the “Service Name” field can reveal suspicious changes.
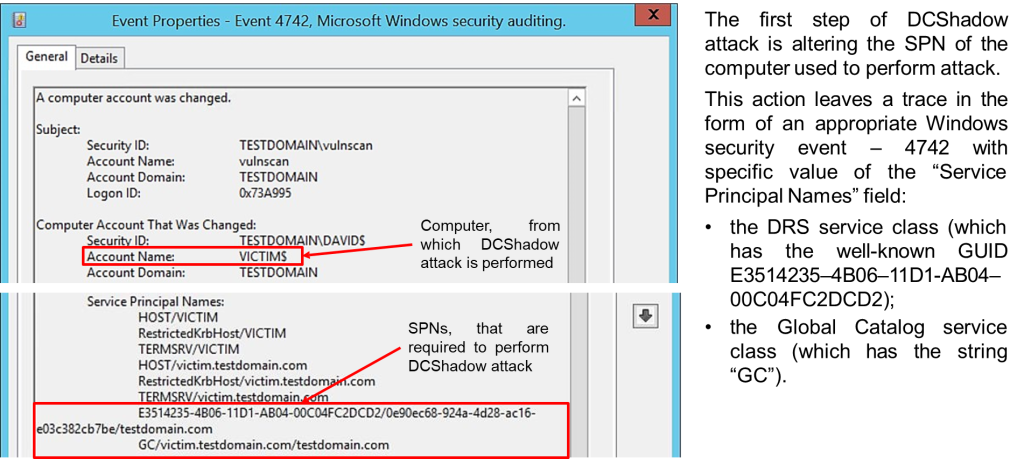
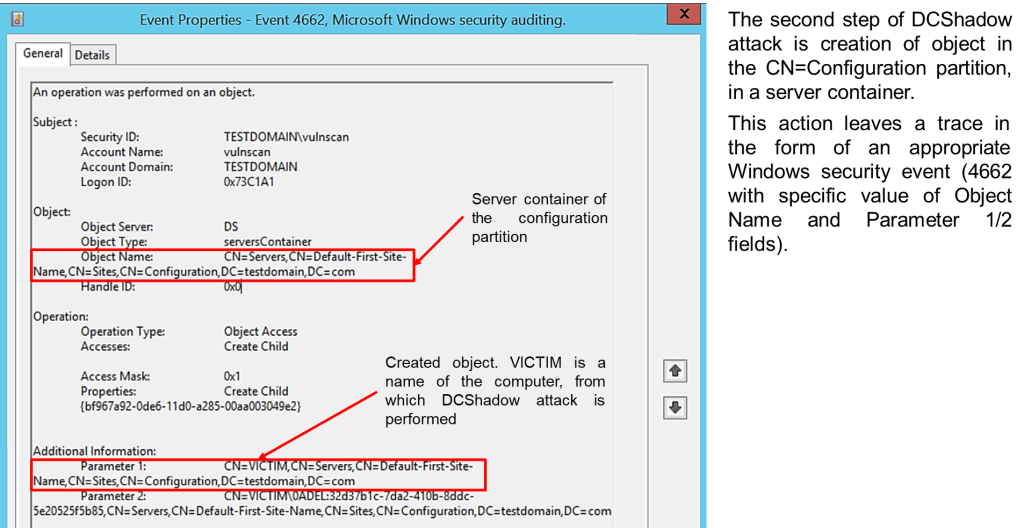
- • Event 4662 (Object Modification): During the attack, the creation of objects in the
CN=Configurationpartition generates event ID 4662, which logs specific object modifications. Monitoring theObject NameandParameter 1/2fields in this event can help identify unusual activity.
- • Event 4662 (Object Modification): During the attack, the creation of objects in the
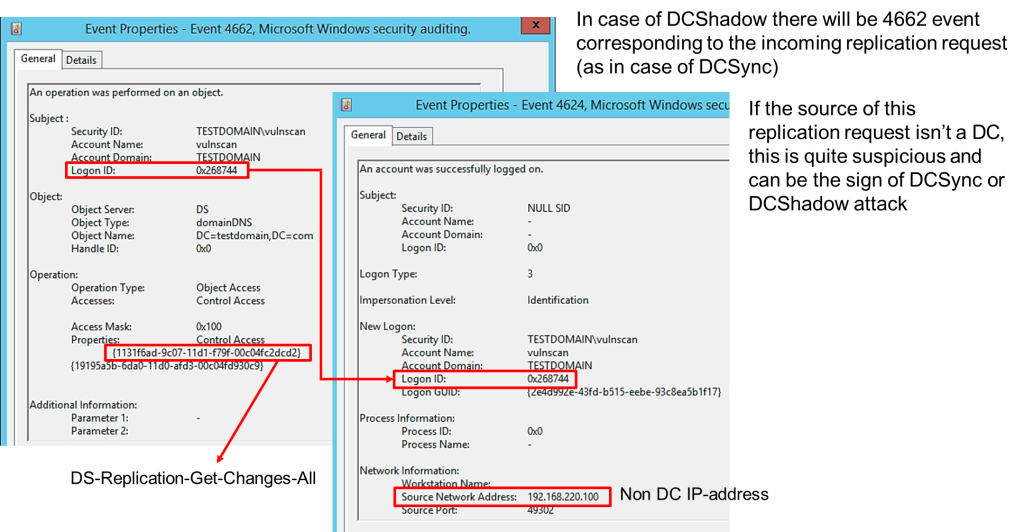
- • Suspicious Replication Requests: Similar to a DCSync attack, DCShadow generates incoming replication requests. A non-DC source triggering these requests is highly suspicious and could indicate an ongoing DCShadow or DCSync attack.
Hunting for DCShadow
• Possible DCShadow attack – suspicious SPN for non DC computer account:
event_id:4742 AND event_data.ServicePrincipalNames:(*E3514235* "*GC/*")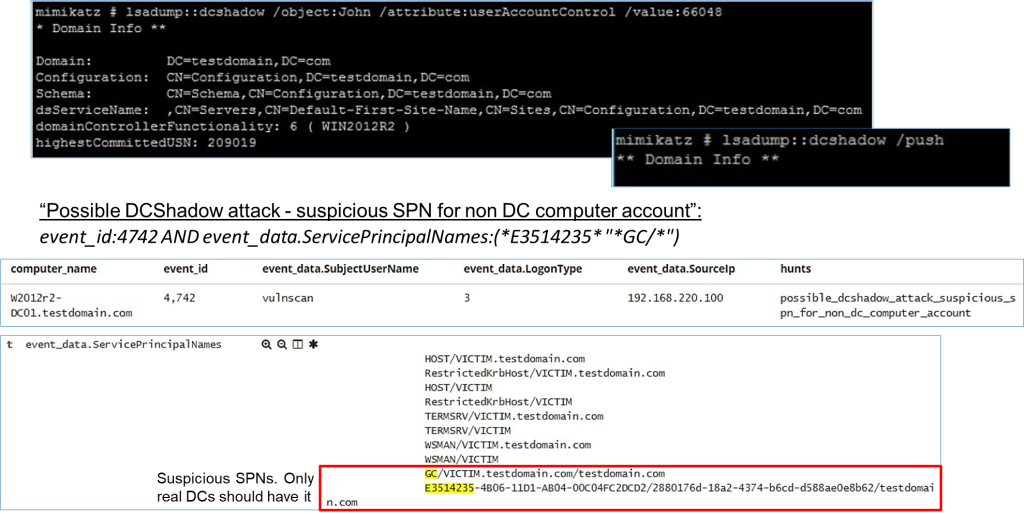
• Possible DCShadow attack – suspicious DC object creation:
event_id:4662 AND event_data.ObjectServer:DS AND -event_data.SubjectUserName:(*DC0*) AND event_data.Properties:"%%7680 {bf967a92-0de6-11d0-a285-00aa003049e2}" AND event_data.AdditionalInfo:"CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration*"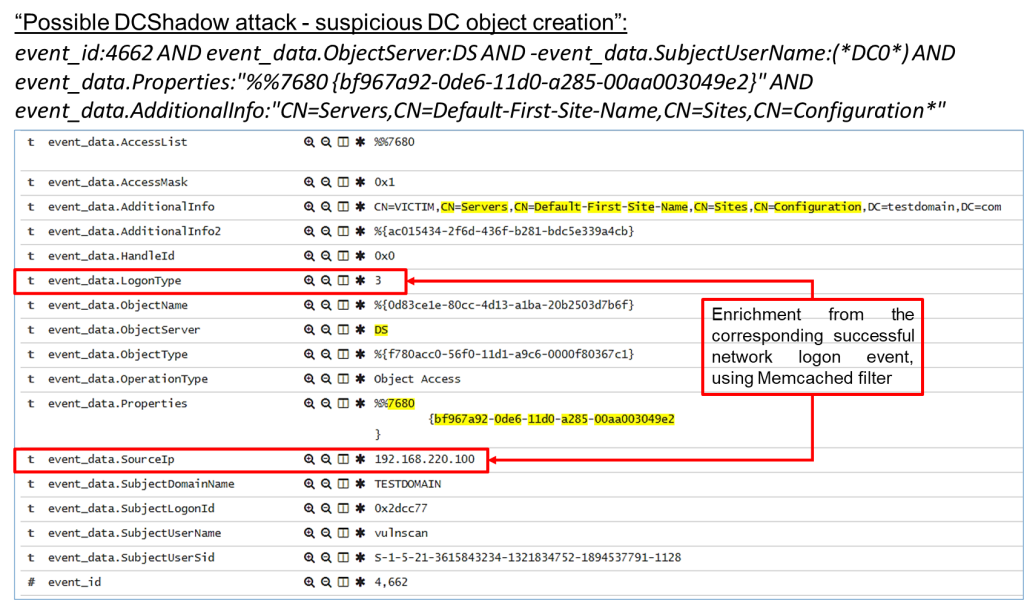
Learn More
To dive deeper into the technical details of DCShadow and how to protect your AD environment, check out the following resources:
Stay vigilant and ensure you have the right detection mechanisms in place to catch these stealthy attacks before they compromise your AD environment!






