Problems with the Classic PICERL Approach
The classic PICERL (Prepare, Identify, Contain, Eradicate, Recover and Lessons Learned) approach to incident response has some theoretical value, but in practice, there are several problems with its execution. One of the most significant issues is that many organizations fail to implement basic security measures during the preparation phase, such as the principle of least privilege and strong passwords. Additionally, network monitoring and log aggregation are often absent, and organizations do not employ threat intelligence as effectively as they could.
Another common problem is a failure to properly scope the incident. Organizations often limit their scope to the systems they already know are compromised, which can be a fatal mistake. Instead, they should scan their entire enterprise for relevant indicators to identify other compromised systems.
Containment is another critical phase that is often improperly executed. Organizations may hasten to kill attacker processes, which can result in vital evidence not being collected, making it more challenging to understand the incident thoroughly. Improper scoping can also contribute to improper containment since the systems where the threat actors have spread to are unknown. All these factors lead to improper eradication, allowing the threat actors to persist in the environment.
When it comes to recovery of business systems, organizations tend to be more thorough. However, during the lessons learned phase, a common problem is not identifying and fixing the root cause of the incident. For example, if a threat actor was able to guess a weak password, the organization must ask why the weak password was allowed in the first place and what needs to be fixed. Is it a weak policy or a lack of enforcement?
These problems highlight the deeper issue with a linear or static approach to incident response. Incidents are often unpredictable and can occur simultaneously, so a rigid approach is not effective. Instead, organizations must adopt a dynamic approach that focuses on outcomes, activities, and waypoints. By doing so, they can detect, triage, and respond to incidents in a timely and efficient manner while continuously improving their incident response process. This approach also enables organizations to adapt to new threats and attack vectors as they emerge, ensuring that their incident response is always up-to-date and effective.
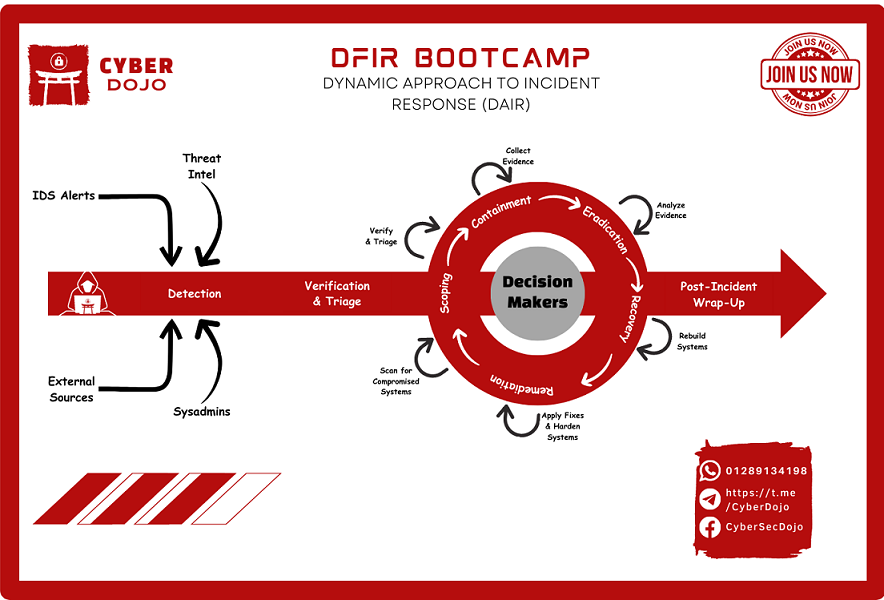
Dynamic Approach to Incident Response (DAIR)
Incident response is a complex process that requires a dynamic and flexible approach. The traditional linear approach, where each step is taken in a specific order, is not effective because incidents are often unpredictable and can occur simultaneously.
Instead, the Dynamic Approach to Incident Response (DAIR) suggests thinking in terms of waypoints, outcomes, and activities. Waypoints are milestones in the incident response process, such as preparation, detection, verification, and triage. These milestones are not necessarily sequential, but rather occur in a cyclical, ongoing process.
For example, detection is an ongoing activity that can come from various sources, including IDS alerts, systems administrators, threat intelligence, and external sources. Once a potential incident is detected, the first step is to verify and perform initial triage. This involves determining the nature and severity of the incident and deciding how to proceed. For instance, responding to a ransomware attack requires a different approach than responding to a threat of workplace violence.
The time between verification and resolution is often murky and requires a flexible approach. Unlike the ideal of PICERL, reality is messy. Rather than thinking in terms of phases, it’s better to focus on outcomes and activities that help achieve those outcomes. For example, scoping involves identifying compromised systems, which may require collecting and examining evidence and scanning the network.
Decisions on what to do next are based on the desired outcomes and available evidence. These decisions require input from both business and security teams and may involve a trade-off between competing priorities, such as minimizing downtime and preserving evidence.
Finally, once the incident is resolved, it’s essential to apply lessons learned to prevent future incidents. This involves conducting a thorough post-incident review, analyzing the incident response process, and identifying areas for improvement. The goal is to continuously refine the incident response process to make it more effective and efficient.
In conclusion, incident response is a complex and ongoing process that requires a dynamic and flexible approach. By thinking in terms of waypoints, outcomes, and activities, organizations can effectively detect, triage, and respond to incidents in a timely and efficient manner while continuously improving their incident response process.
🚀 Ready to elevate your Digital Forensics and Incident Response skills?
Cyber Dojo’s DFIR Bootcamp is here to equip you with the expertise to thrive in the cybersecurity field. Cyber Dojo offers a DFIR Bootcamp that combines GCFE Preparation (FOR500) and GCIH Preparation (SEC504), this intensive course combines in-depth knowledge and hands-on practice, giving you the tools and confidence to tackle real-world DFIR challenges.
Take the next step in your cybersecurity career—join our DFIR Bootcamp and gain the edge you need to succeed! 🔍🛡️
Click on the link to view or DFIR Bootcamp: DFIR Bootcamp – Cyber Dojo